中国科学技术大学第八届信息安全大赛
去吧!追寻自由的电波
音乐人狂喜(
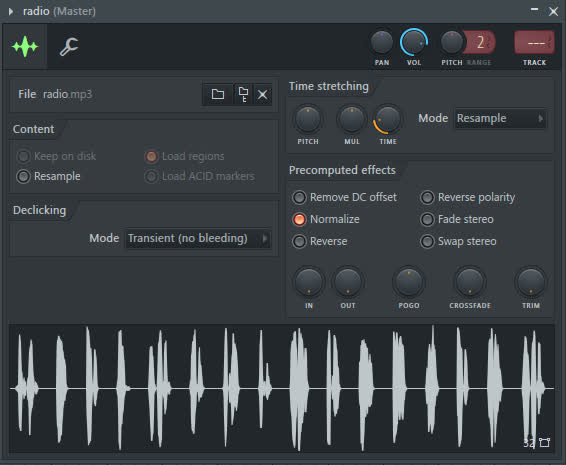
使用保卫萝卜( )在Resample模式下调整TIME即可,顺便可以来个Normalize
)在Resample模式下调整TIME即可,顺便可以来个Normalize
透明的文件
‘[‘替换成0x1b即可。
以前在写控制台库的时候整过。
FLAG 助力大红包
from time import sleep
import requests as req
def fuck_ip(ip_addr):
return req.post(
"http://202.38.93.111:10888/invite/bf620d77-6562-4179-863b-a3901ff6b5b9",
data={'ip': ip_addr},
headers={
'X-Forwarded-For': ip_addr
}
)
if __name__ == '__main__':
rip = set()
for i in range(0, 256):
ip = f'{i}.0.0.0'
ret = fuck_ip(ip).text
if '快' in ret:
rip.add(ip)
print(ret)
sleep(1.5)
print(rip)Amnesia
轻度失忆
#include <stdio.h>
#define _ putchar
int main() {_('H');_('e');_('l');_('l');_('o');_(',');_(' ');_('w');_('o');_('r');_('l');_('d');_('!');}Easy RSA
(* 不会数论,选择使用Mathematica解决问题 *)
(* 已知x、y,可求出p,参考https://www.geeksforgeeks.org/modular-exponentiation-power-in-modular-arithmetic/ *)
p = NextPrime[Fold[Mod[#1 * ModularInverse[#2, x], x] &, x - 1, Range[y + 1, x - 1]]];
(* 参考RSA原理可求出q *)
(* value10是value[-1] *)
value = NextPrime[value10, #] & /@ Range[-9, 0];
NCESolveM[nv_, c_, e_] := PowerMod[c, ModularInverse[e, Times @@ ((# - 1) & /@ nv)], Times @@ nv];
q = NextPrime[NCESolveM[value, valueQ, e]];
(* 已知p、q、c、e,根据RSA原理求出m *)
m = NCESolveM[{p, q}, c, e];
(* 转成字符串即可得到flag *)
StringJoin @@ (FromCharacterCode[FromDigits[#, 16]] &) /@ StringJoin /@ Partition[Characters[IntegerString[m, 16]], 2]
python验证
import sympy
from operator import mul
from functools import reduce
def egcd(a, b):
if a == 0:
return (b, 0, 1)
else:
g, y, x = egcd(b % a, a)
return g, x - (b // a) * y, y
def inverse_mod(a, m):
g, x, y = egcd(a, m)
if g != 1:
raise Exception('modular inverse does not exist')
else:
return x % m
def FuckRsaFactored(primes, n, c, e):
d = inverse_mod(e, reduce(mul, [i - 1 for i in primes]))
m = pow(c, d, n)
return m
def modFact(n, p):
if (p <= n):
return 0
res = (p - 1)
for i in range(n + 1, p):
res = (res * inverse_mod(i, p)) % p
return res
e = 65537
def get_p():
x = 11124440021748127159092076861405454814981575144744508857178576572929321435002942998531420985771090167262256877805902135304112271641074498386662361391760451
y = 11124440021748127159092076861405454814981575144744508857178576572929321435002942998531420985771090167262256877805902135304112271641074498386662361391661439
# value_p = sympy.nextprime((math.factorial(y)) % x) # Hint:这里直接计算会溢出,请你仔细观察 x 和 y 的特征
return sympy.nextprime(modFact(y, x))
def get_q():
# value = [getPrime(256)]
value = [80096058210213458444437404275177554701604739094679033012396452382975889905121]
for i in range(1, 10):
value.append(sympy.nextprime(value[i - 1]))
# q[-1] = 80096058210213458444437404275177554701604739094679033012396452382975889905967
assert value[-1] == 80096058210213458444437404275177554701604739094679033012396452382975889905967
n = 1
for i in range(10):
n = n * value[i]
# q = getPrime(512)
q = FuckRsaFactored(value, n,
5591130088089053683141520294620171646179623062803708281023766040254675625012293743465254007970358536660934858789388093688621793201658889399155357407224541324547522479617669812322262372851929223461622559971534394847970366311206823328200747893961649255426063204482192349202005330622561575868946656570678176047822163692259375233925446556338917358118222905050574458037965803154233167594946713038301249145097770337253930655681648299249481985768272321820718607757023350742647019762122572886601905212830744868048802864679734428398229280780215896045509020793530842541217790352661324630048261329493088812057300480085895399922301827190211956061083460036781018660201163819104150988531352228650991733072010425499238731811243310625701946882701082178190402011133439065106720309788819,
e)
# q = 774618558248818670631844032267012933902957533188887861123117351257918290746681030265456412784328215912450280395013228966479783450877253924424423961716903439226728415764994065594433231325380628079830946408174666851026540651999835226740834648841884584099434263657860352894358875465848621861291648191833890366381090644139344996600343764226314671451476799640110582009409520743816771317014575031963482104152201836469468926224678429266089921372754086505357097142947219341363848966815329678678379841179969404701386591136776428275184515113810107722648703989768128328235085899193443308603379772286906627487171331652282150891526597993057659101306912979951255724909969698121538885140089890845520476265621512764521645257280377023106240706462006692932021286389765181708059526596297
value_q = pow(q, e, n)
# value_q = 5591130088089053683141520294620171646179623062803708281023766040254675625012293743465254007970358536660934858789388093688621793201658889399155357407224541324547522479617669812322262372851929223461622559971534394847970366311206823328200747893961649255426063204482192349202005330622561575868946656570678176047822163692259375233925446556338917358118222905050574458037965803154233167594946713038301249145097770337253930655681648299249481985768272321820718607757023350742647019762122572886601905212830744868048802864679734428398229280780215896045509020793530842541217790352661324630048261329493088812057300480085895399922301827190211956061083460036781018660201163819104150988531352228650991733072010425499238731811243310625701946882701082178190402011133439065106720309788819
assert value_q == 5591130088089053683141520294620171646179623062803708281023766040254675625012293743465254007970358536660934858789388093688621793201658889399155357407224541324547522479617669812322262372851929223461622559971534394847970366311206823328200747893961649255426063204482192349202005330622561575868946656570678176047822163692259375233925446556338917358118222905050574458037965803154233167594946713038301249145097770337253930655681648299249481985768272321820718607757023350742647019762122572886601905212830744868048802864679734428398229280780215896045509020793530842541217790352661324630048261329493088812057300480085895399922301827190211956061083460036781018660201163819104150988531352228650991733072010425499238731811243310625701946882701082178190402011133439065106720309788819
return sympy.nextprime(q)
# this destroyes the rsa cryptosystem
p = get_p()
q = get_q()
n = p * q
print("---- pre ----")
print("p = ", p)
print("q = ", q)
print("n = ", n)
print("e = ", e)
# m = int.from_bytes(open("flag.txt", "rb").read(), "big")
m = FuckRsaFactored([p, q], p * q,
110644875422336073350488613774418819991169603750711465190260581119043921549811353108399064284589038384540018965816137286856268590507418636799746759551009749004176545414118128330198437101472882906564195341277423007542422286760940374859966152871273887950174522820162832774361714668826122465471705166574184367478,
e)
c = pow(m, e, n)
print("c = ", c)
assert c == 110644875422336073350488613774418819991169603750711465190260581119043921549811353108399064284589038384540018965816137286856268590507418636799746759551009749004176545414118128330198437101472882906564195341277423007542422286760940374859966152871273887950174522820162832774361714668826122465471705166574184367478
# c = 110644875422336073350488613774418819991169603750711465190260581119043921549811353108399064284589038384540018965816137286856268590507418636799746759551009749004176545414118128330198437101472882906564195341277423007542422286760940374859966152871273887950174522820162832774361714668826122465471705166574184367478
print("----done----")
print("m = ", m)
print(m.to_bytes(len(hex(m)) // 2 - 1, 'big').decode())
加密的 U 盘
直接阅读LUKS2手册,发现更换密码不修改master key,所以把day1的密码套到day2上就行,使用winhex把day1的LUKS Header覆盖day2的 LUKS Header,最后正常挂载即可发现flag
minecRaft
发现flag.js,分析一下就能发现是XTEA,直接写出解密函数
function decode(v, key) {
let v0=v[0];
let v1=v[1];
const delta=0x9E3779B9;
let sum = delta * 0x20;
for (let i = 0; i < 0x20; ++i)
{
v1 -= (v0 << 0x4 ^ v0 >>> 0x5) + v0 ^ sum + key[sum >>> 0xb & 0x3];
sum -= delta;
v0 -= (v1 << 0x4 ^ v1 >>> 0x5) + v1 ^ sum + key[sum & 0x3];
}
return [v0,v1];
}可以使用暴力清除定时器
[...Array(100).keys()].forEach(x => clearInterval(x))key可以断点获得 ,然后在浏览器控制台执行即可获取flag
[...Array(4).keys()].map(i=>'6fbde674819a59bfa12092565b4ca2a7a11dc670c678681daf4afb6704b82f0c'.substr(i*16,16)).map(x=>[...Array(2).keys()].map(i=>Base16ToLong(x.substr(i*8,8)))).map(v=>decode(v, [909456177,825439544,892352820,926364468]).map(LongToStr4).join('')).join('')
太忙了,基本没时间打,整天被资本家压榨